
In an era of unprecedented digital transformation, traditional cybersecurity models are struggling to keep up with sophisticated cyber threats.
The rise of Zero Trust Security represents a major shift in cyber governance, providing a strong framework that is vital for protecting sensitive data and ensuring the integrity of digital operations.
This innovative approach is not only essential for modern cyber governance, but also signifies a fundamental change in how organizations view and implement security measures.
Understanding Zero Trust Security
Zero Trust Security is a cybersecurity model based on the principle of “never trust, always verify.” Unlike traditional security models that focus on defending the network perimeter, Zero Trust assumes that threats can be both external and internal.
Therefore, every access request, whether from within or outside the network, must be authenticated, authorized, and continuously validated.
This model relies heavily on strict identity verification, micro-segmentation, and the principle of least privilege. By continuously monitoring and validating user identities and device integrity, Zero Trust minimizes the risk of unauthorized access and data breaches.
Implementing granular access controls ensures that even if an attacker gains access to the network, their movement is severely restricted.
The Need for Zero Trust Security in the Digital Age
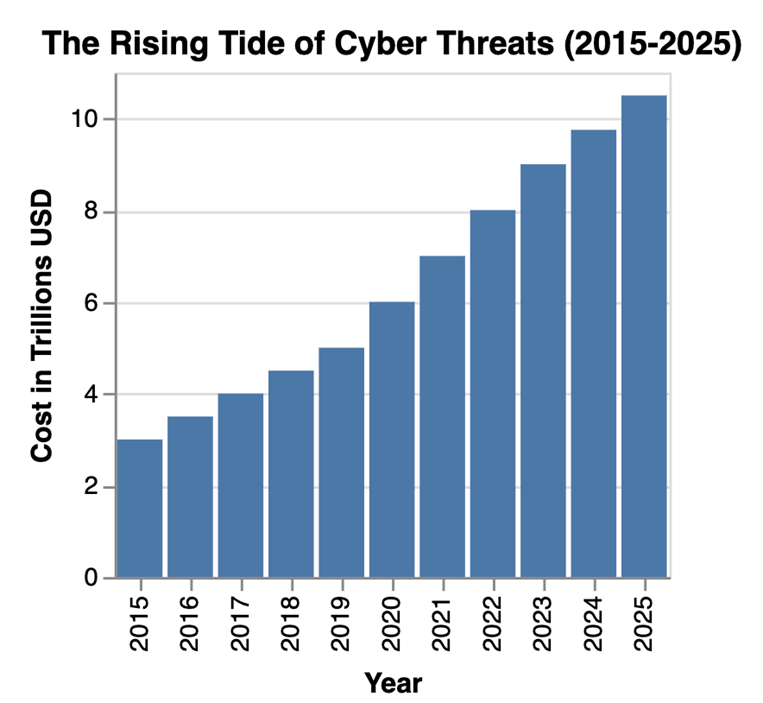
The digital landscape is evolving rapidly with the adoption of cloud computing, IoT devices, and remote work environments. This evolution has blurred the traditional network perimeter, making organizations more vulnerable to cyber threats. According to a report by Cybersecurity Ventures, cybercrime is predicted to cost the world $10.5 trillion annually by 2025, up from $3 trillion in 2015 (https://esentire.com)
Zero Trust Security addresses these challenges by providing a comprehensive security framework that adapts to the complexities of modern IT environments. By enforcing continuous authentication and authorization, it reduces the attack surface and enhances the organization’s ability to detect and respond to threats in real time.
Implementing Zero Trust Security: Best Practices
Adopting Zero Trust Security requires a strategic approach and a paradigm shift in how organizations perceive cyber security. Here are some best practices to guide the implementation of this model:
1. Identify and Classify Assets: Begin by mapping out all digital assets, including data, applications, and devices. Classify them based on their sensitivity and criticality to the business.
2. Enforce Multi-Factor Authentication (MFA): Strengthen access controls by requiring multiple forms of verification for all users, particularly for access to sensitive systems.
3. Micro-Segmentation: Divide the network into smaller, isolated segments to limit lateral movement by attackers. Apply specific security policies to each segment based on its risk profile.
4. Continuous Monitoring and Analytics: Implement tools that provide real-time visibility into network traffic and user behavior. Use analytics to detect anomalies and potential threats.
5. Adopt a Least-Privilege Model: Ensure that users and applications have the minimum level of access necessary to perform their functions. Regularly review and adjust access rights to align with current roles and responsibilities.
6. Educate and Train Employees: Cybersecurity is a collective responsibility. Conduct regular training sessions to educate employees about security best practices and the importance of following Zero Trust principles.
The Role of an MBA with Cyber Governance and Law
For professionals aiming to excel in the dynamic field of cybersecurity, specialized education is crucial. The MBA with Cyber Governance and Law is designed to equip professionals with the skills and knowledge required to navigate modern cybersecurity challenges. This program covers critical areas such as risk management, legal aspects of cybersecurity, and the implementation of security frameworks like Zero Trust.
By integrating theoretical knowledge with practical insights, the MBA program prepares students to develop and lead effective cybersecurity strategies within their organizations. Graduates of this program are well-positioned to drive the adoption of Zero Trust principles, ensuring their organizations remain resilient in the face of evolving cyber threats. The comprehensive curriculum not only enhances technical expertise but also hones leadership and strategic thinking skills, paving the way for career advancement in the field of cyber governance.
Zero Trust Security is revolutionizing cyber governance in the digital age by overcoming the shortcomings of traditional security models and offering a strong framework to combat modern cyber threats. As organizations increasingly undergo digital transformation, it becomes crucial to adopt Zero Trust principles to protect critical assets and uphold operational integrity.
The MBA with Cyber Governance and Law from Westford Uni Online, in collaboration with Abertay University is designed for professionals who want to make a significant impact in the field. It offers an ideal mix of education and practical application. Graduates pursuing this program can look forward to mastering the principles of Zero Trust and other advanced security frameworks, enabling them to lead their organizations towards a more secure and resilient digital future.





